Briefly Describe the Best Practice Rules for Firewall Use.
Essential feature turned on to save money b. Or Firewall can be described as a set of rules which helps in preventing un-authorized access to users personal networks.
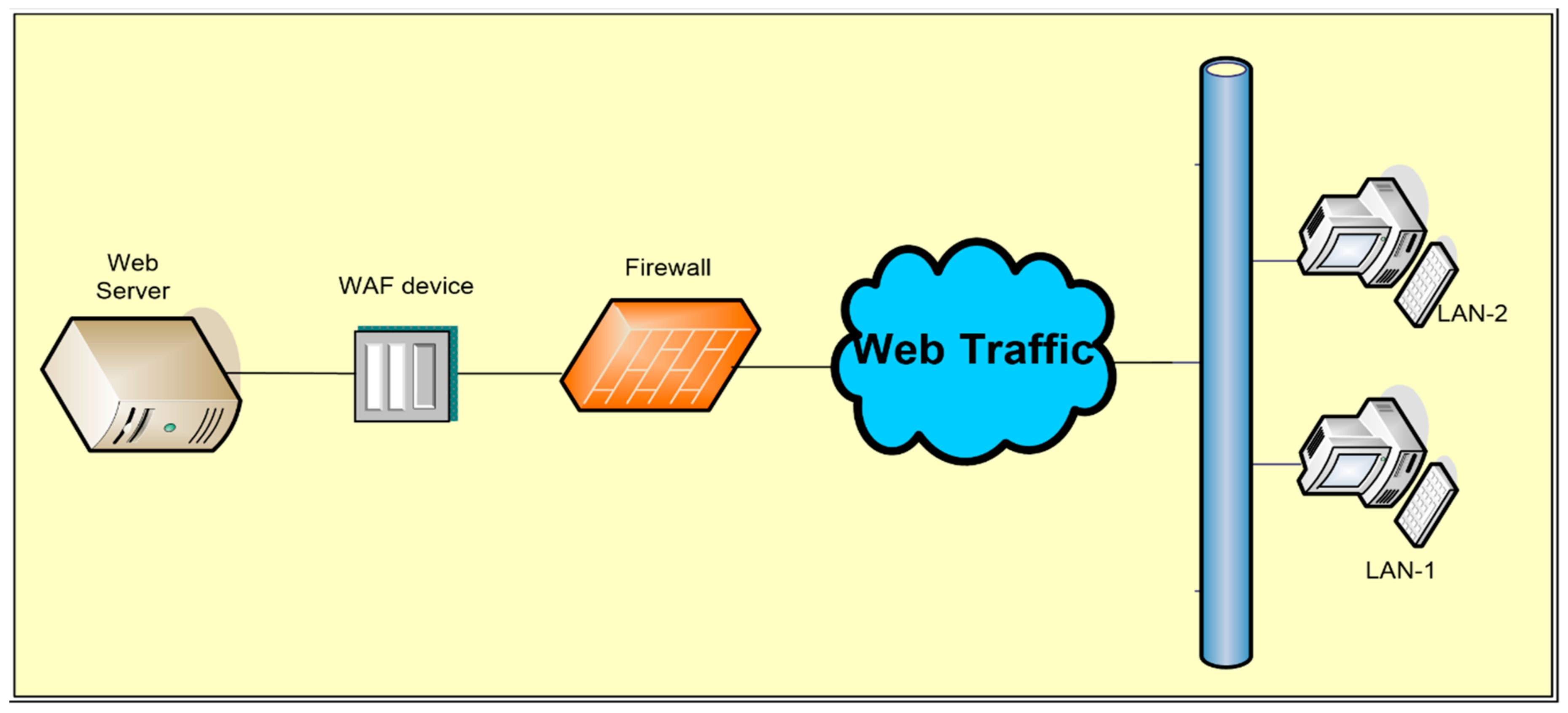
Applied Sciences Free Full Text Firewall Best Practices For Securing Smart Healthcare Environment A Review Html
This reduces your risk gives you more control over your traffic and limits your communication between.

. View solution in original post. We can describe firewall as a system which is designed to prevent unwanted users to access the computer network. These types of software may be harmful for our system.
Known as the ping service ICMP is an _____ and should be _____. Known as the ping service ICMP is an _____ and should be _____. 105 Briefly describe the best practice rules for firewall use Graders Info 1 All from ICT 125 at Dublin City University.
Prohibit the federal government from requiring the use of encryption for contracts grants and other official documents and correspondence. The firewall device is never directly accessible form the public network for configuration or management purposes. False When Web services are offered outside the firewall SMTP traffic should be blocked from internal networks through the use of some form of proxy access or DMZ architecture.
Briefly describe the best practice rules for firewall use. We help companies worldwide automate and streamline complex tasks ensure network health and performance achieve business continuity and do more with fewer resources. Best Practices For Configuring Firewall Rules.
Briefly describe the best practice rules for firewall use. We review their content and use your feedback to keep the quality high. Reinforce an individuals right to use or sell encryption algorithms without concern.
Briefly describe the best practice rules for firewall use. Provide the choices an organization has when setting policy on how to employ digital forensics. Best Practices and Recommendations for Firewall Rules.
Briefly describe the best practice rules for firewall use. Essentially it acts when it detects the given condition matched. These recommendations cover a wide range of deployments including home networks and enterprise desktopserver systems.
Question 1 Needs Grading Briefly describe the seven best practices. Suppose that the Internet traffic matches the components of a rule. To open Windows Firewall go to the Start menu select Run type WFmsc and then select OK.
View Test Prep - ISYS 331 Week 3 quiz 6docx from ISYS 331 at Regent University. Provide the choices an organization has when setting policy on how to employ digital forensics. Just remember to also configure your VPN-rules if a VLAN should also be not allowed to communicate through the VPN.
Question 35 Your Answer Briefly describe the seven best practices rules for from AA 1. Briefly describe the seven best practices rules for firewall use. Essential feature turned on to save money b.
BackBox is a market leader in network automation security and management solutions. What are Best Practices for Firewall Rules Configuration. A network administrator must design a security policy that describes all of the network resources within a company and the required security level for those resources in order to safeguard the network.
We use various types of software which are downloaded from internet. Dont complicate firewall management by unnecessarily nesting rule objects. Avoid using the Any option in the firewalls Allow rules.
Briefly describe the best practice rules for firewall use. 03-16-2021 1015 AM. Try to use the same rule set for similar firewall policies with the same group object.
In general you should follow the best practice of least privilege when configuring a firewall which just means to block literally everything that you arent using for a dedicated and approved business function. So I want to know about details of firewall. We use the Firewall tools for security reasons.
Add expiry dates as comments for temporary rules and regularly review these dates for rule clean-up. Configuring your Windows Firewall based on the following best practices can help you optimize protection for devices in your network. A secure network is critical to a companys success.
Briefly describe the best practice rules for firewall use. Firewall rules define the active component that decides what Internet traffic it will permit and what Internet traffic it will block. Common method for hacker reconnaissance turned off to.
All traffic from the trusted network is allowed out. Briefly describe the seven best practices rules for firewall use. I would use the rules on the Firewall-page of the MX.
All traffic from the trusted network is allowed out. State that the use of encryption is not probable cause to suspect criminal activity. These rule work statefully any return-traffic is automatically allowed.
__________ firewalls are designed to operate at the media access control sublayer of the data link layer of the OSI network model. The firewall device is never directly accessible from the public network for configuration or management purposes. 100 1 rating Firewall.
Your Answer Briefly describe the seven best practices rules for firewall use 1 from AA 1.

What Is A Firewall Definition Key Components And Best Practices Toolbox It Security
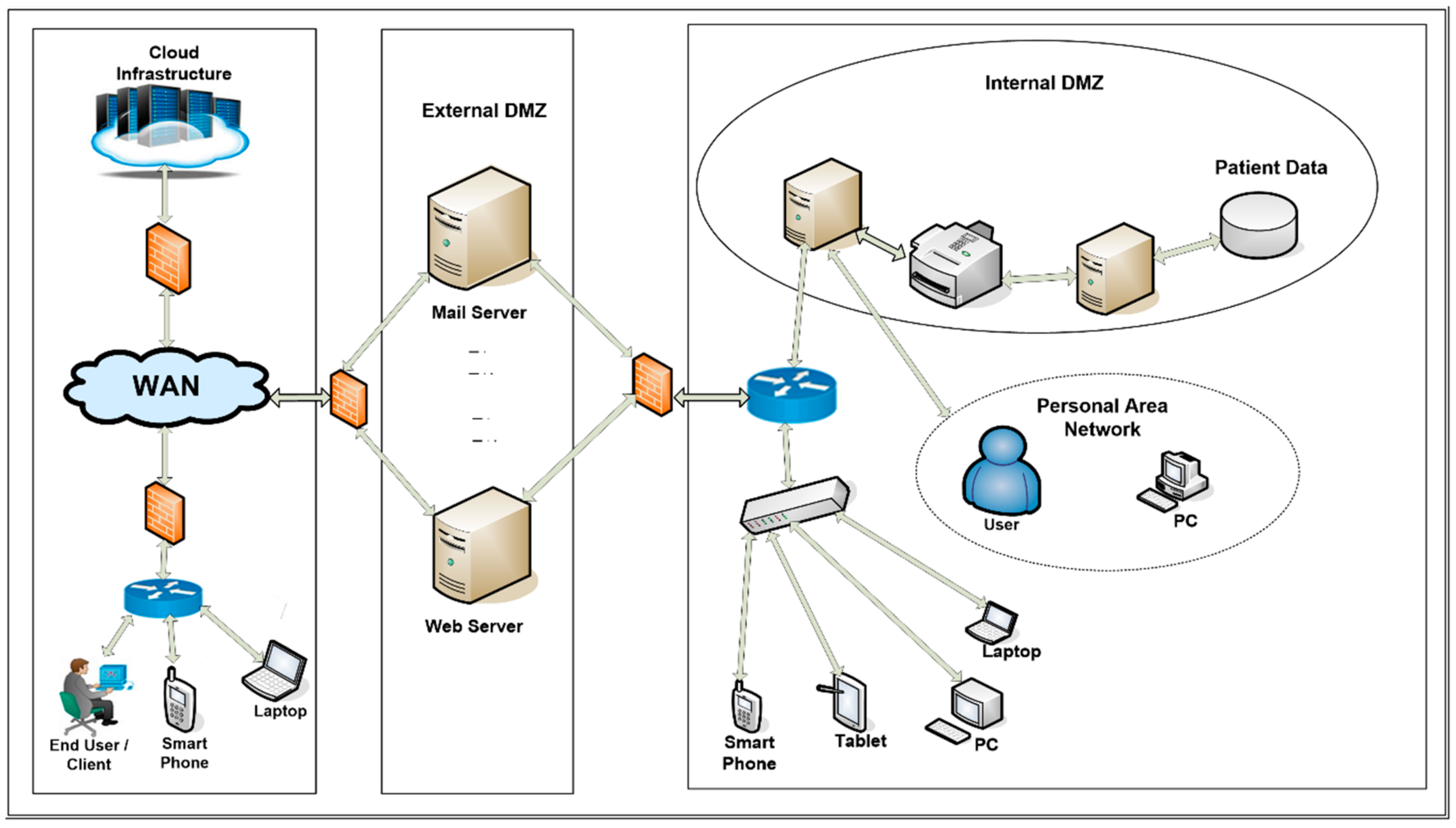
Applied Sciences Free Full Text Firewall Best Practices For Securing Smart Healthcare Environment A Review Html

What Is Email Security Definition Benefits Examples Best Practices Toolbox It Security
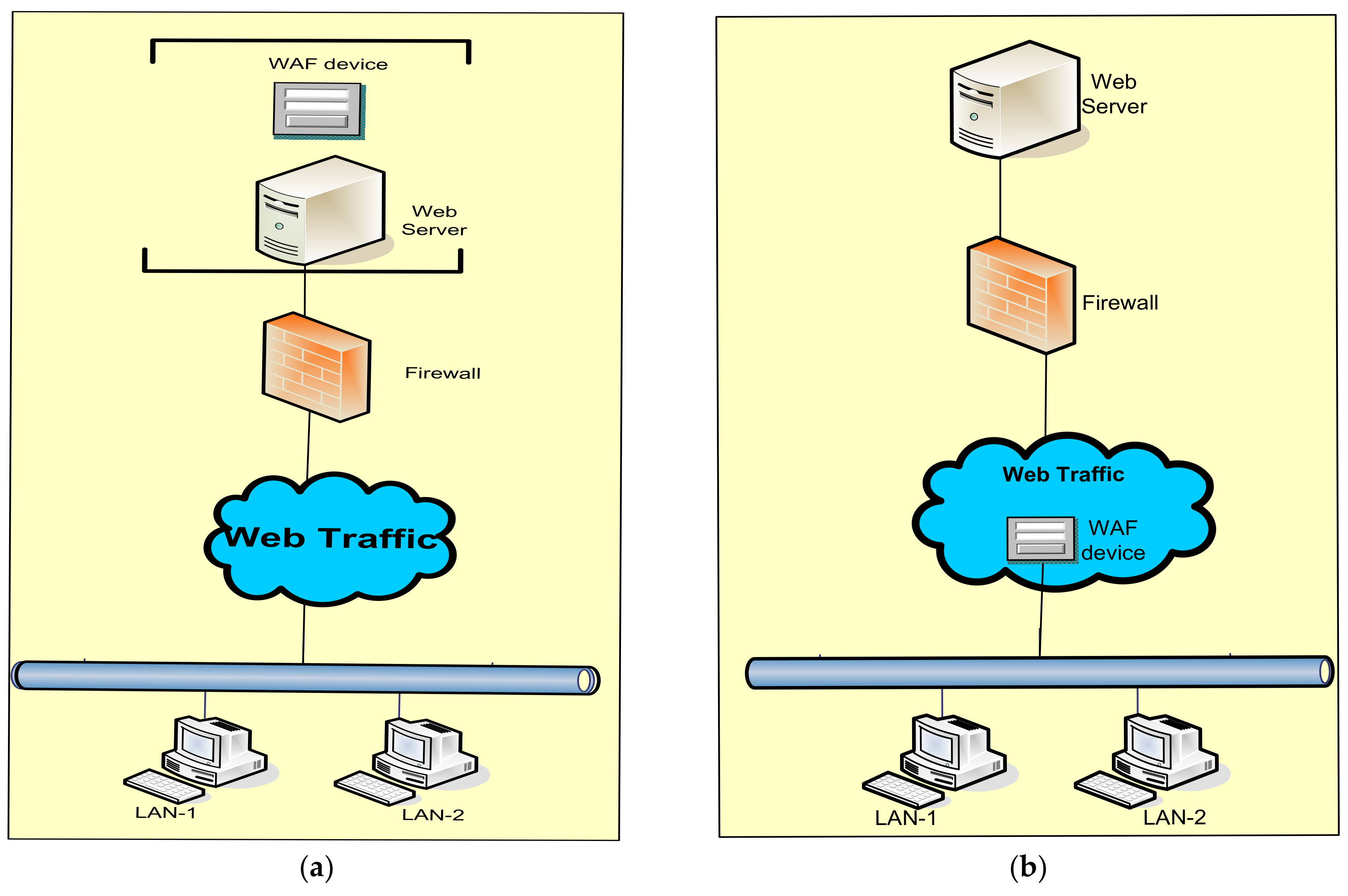
Applied Sciences Free Full Text Firewall Best Practices For Securing Smart Healthcare Environment A Review Html
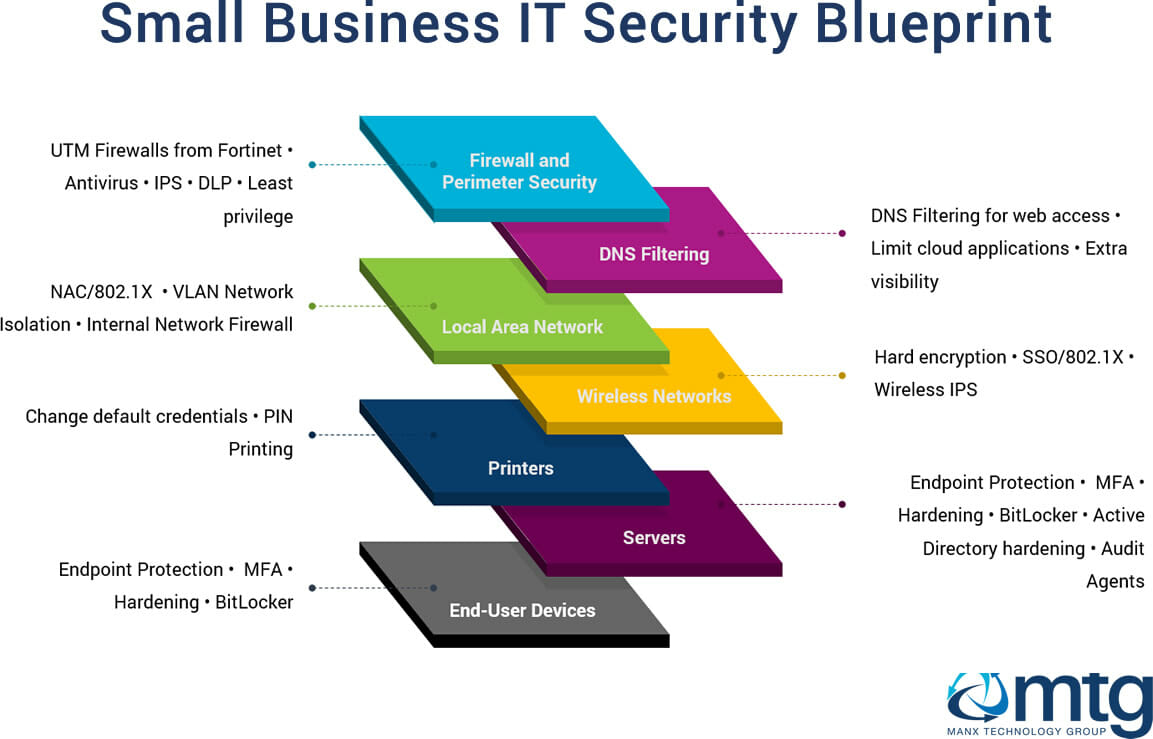
Small Business It Security Guide Manx Technology Group

7 Best Practices For Securing System Administrator Privileged Account Ekran System
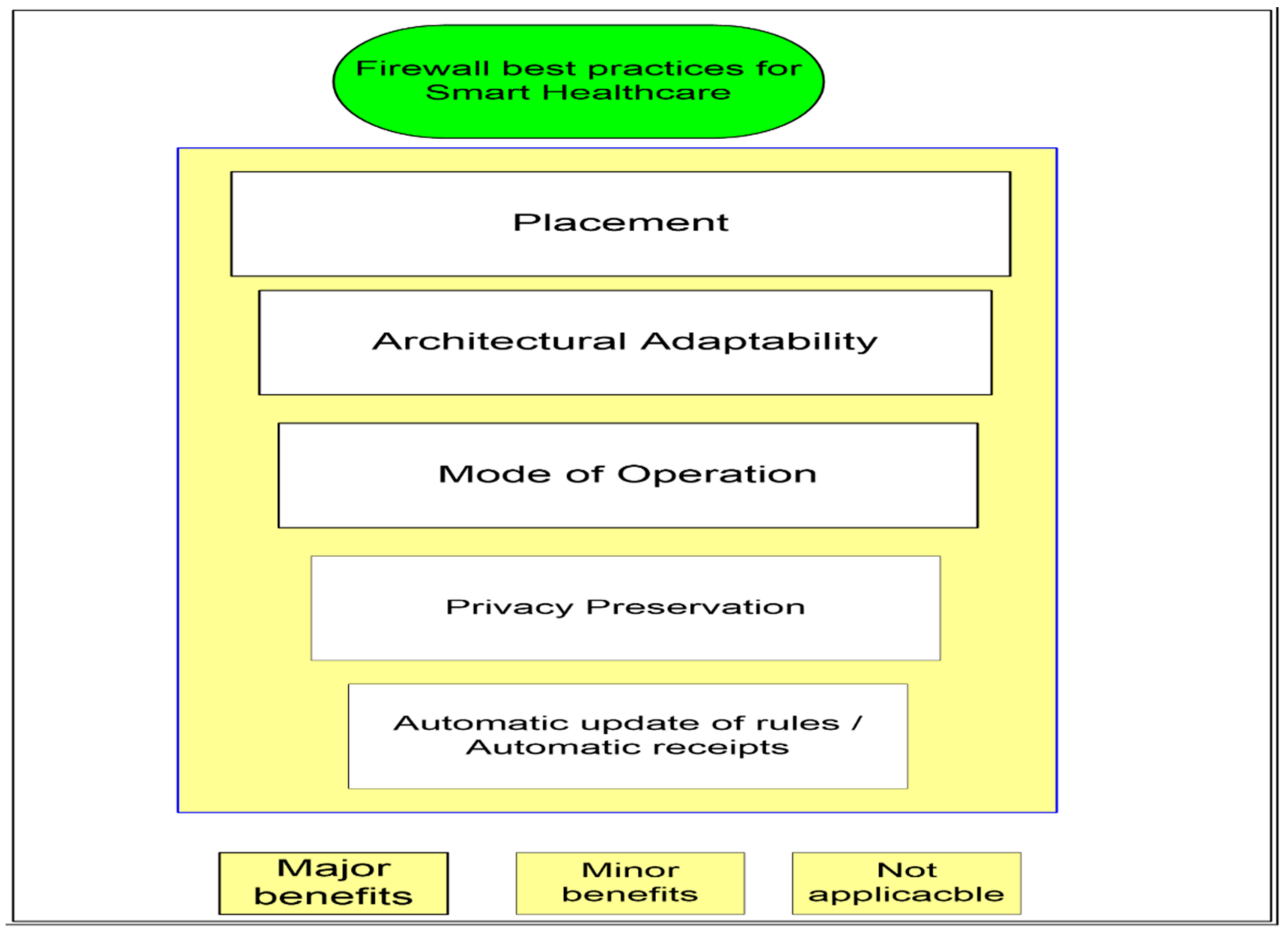
Applied Sciences Free Full Text Firewall Best Practices For Securing Smart Healthcare Environment A Review Html
Secure Software Development Best Practices And Methodologies For Secure Sdl Lifecycle

7 Best Practices For Securing System Administrator Privileged Account Ekran System
Top 10 Cybersecurity Best Practices For Your Business Touro College Illinois

Cybersecurity Ot A Comprehensive Guide

Azure Security Best Practices You Need To Know Cloud Academy
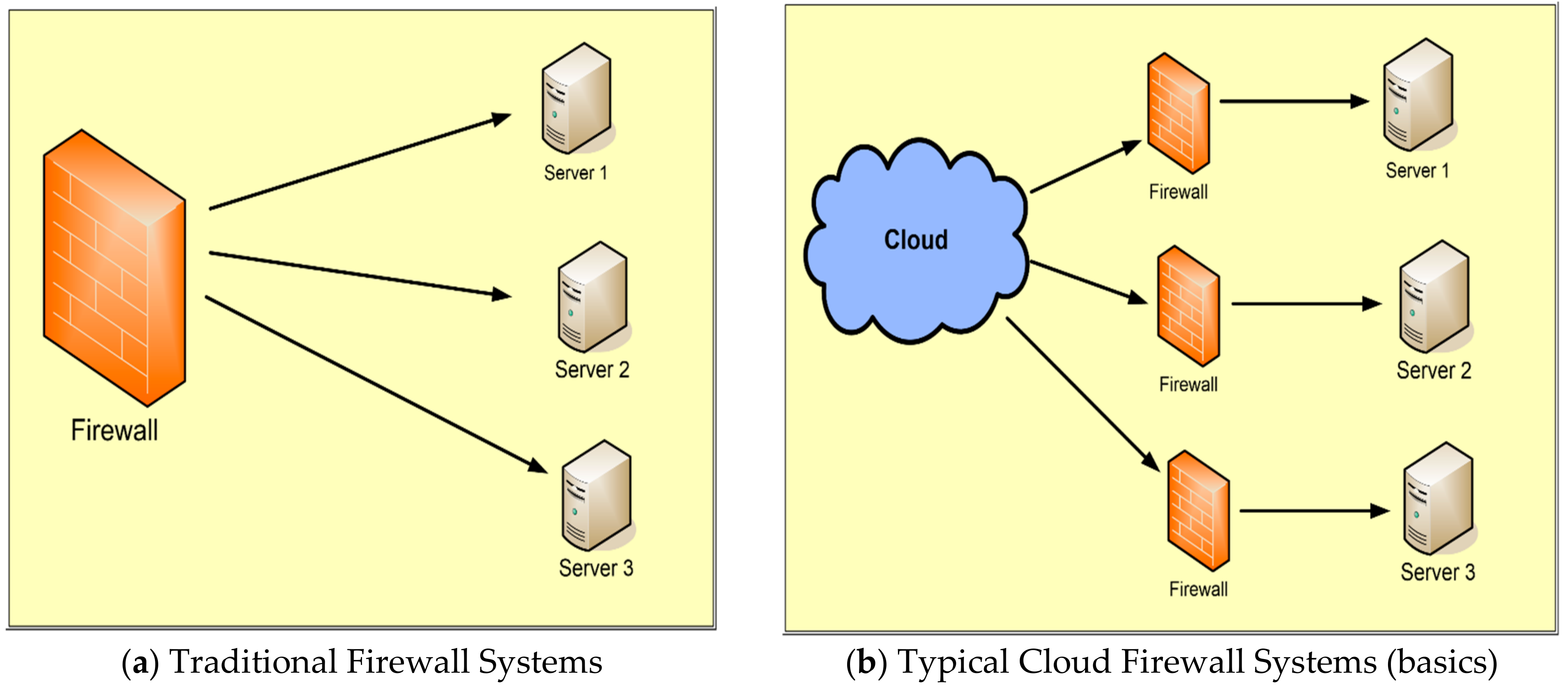
Applied Sciences Free Full Text Firewall Best Practices For Securing Smart Healthcare Environment A Review Html

7 Best Practices For Securing System Administrator Privileged Account Ekran System
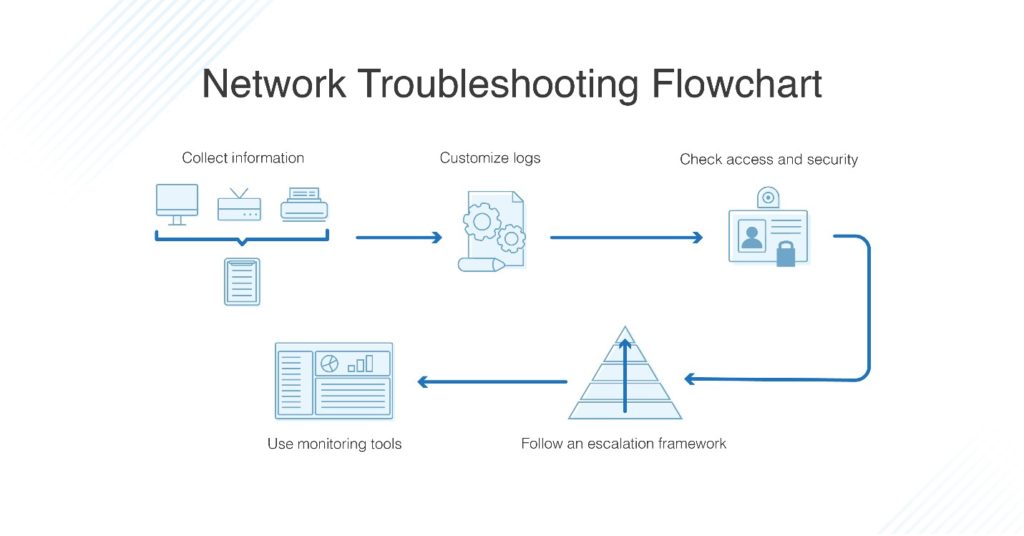
Network Troubleshooting Steps Techniques Best Practices Dnsstuff
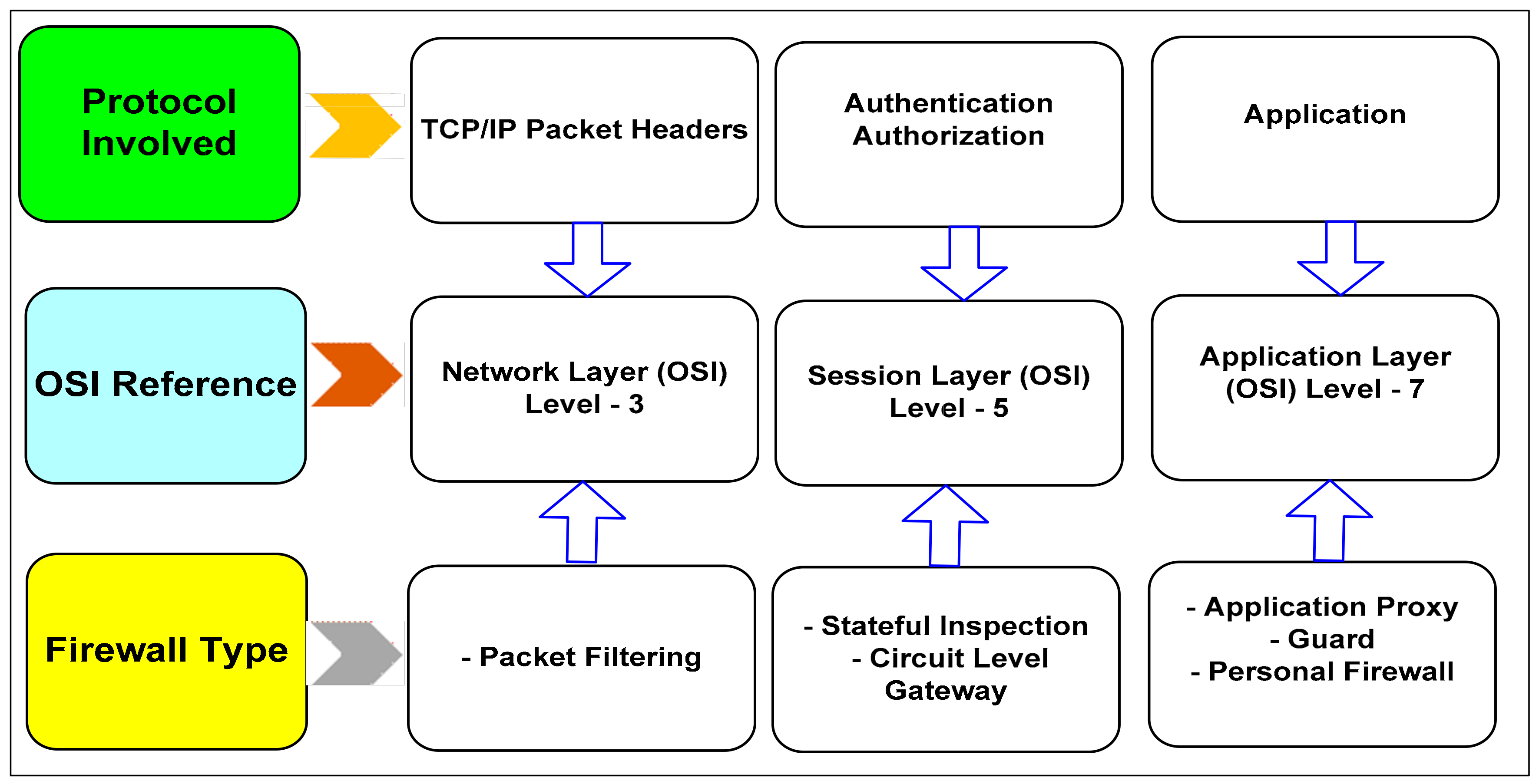
Applied Sciences Free Full Text Firewall Best Practices For Securing Smart Healthcare Environment A Review Html
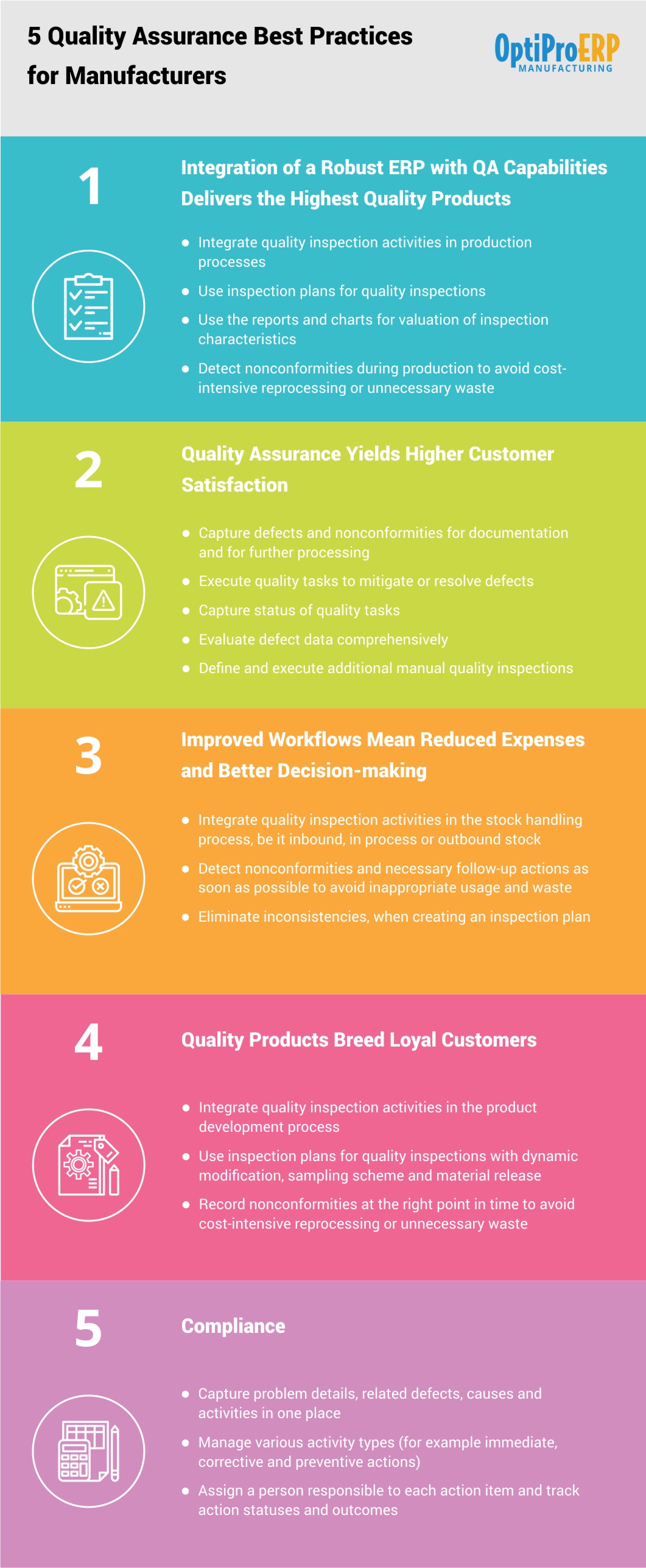
5 Quality Assurance Best Practices For Manufacturers Optiproerp

Comments
Post a Comment